Cyberattacks: Page 24
-
Sponsored by Delinea
How do I monitor privileged accounts?
Are you monitoring your privileged accounts? Start here to shield your organization against attacks.
By Tony Goulding • Sept. 12, 2022 -

 Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
CISA announces RFI for critical infrastructure cyber reporting mandate
The agency plans to publish the information request in the Federal Register on Monday and will kick off a national listening tour.
By David Jones • Sept. 9, 2022 -
 Explore the Trendline➔
Explore the Trendline➔
 BNMK0819 via Getty Images
BNMK0819 via Getty Images Trendline
TrendlineTop 5 stories from Cybersecurity Dive
A wave of rules, regulations and federal action is putting pressure on businesses to shore up security amid a backdrop of emboldened threat actors has a nice ring to it.
By Cybersecurity Dive staff -


Website of medical device sales form: https://spwindustrial.com/baxter-sigma-spectrum-infusion-pump-s-w-ver-8-with-dual-antenna-wireless-batt/?gclid=Cj0KCQjwpeaYBhDXARIsAEzItbFttwA55ImqoesvcmNYfm6od_td4SGgOeNOqFOQohCiU_ci1yN-oHsaAqiFEALw_wcB

CISA issues advisory after vulnerabilities found on Baxter infusion pumps
The weaknesses could allow attackers to access WiFi data and make the device unavailable.
By Nick Paul Taylor • Updated Sept. 8, 2022 -
Healthcare fintechs targeted by cybercriminals
Cybersecurity professionals say healthcare payments processing firms are particularly vulnerable to information technology breaches and ransomware attacks.
By Joe Burns • Sept. 8, 2022 -
Los Angeles school district hit by ransomware attack
Schools reopened after the holiday weekend but many IT systems remain inaccessible. A districtwide password reset is underway.
By Matt Kapko • Sept. 6, 2022 -
Email hacking scheme leads to attempted theft of $13M from Pennsylvania school district
Local government agencies intercepted and recovered $10.3 million in funds stolen from Chester Upland School District.
By Anna Merod • Sept. 6, 2022 -
Most organizations remain unprepared for ransomware attacks
Too many organizations are failing to meet cybersecurity demands. Ransomware attacks abound and humans are still the weakest link.
By Matt Kapko • Sept. 6, 2022 -
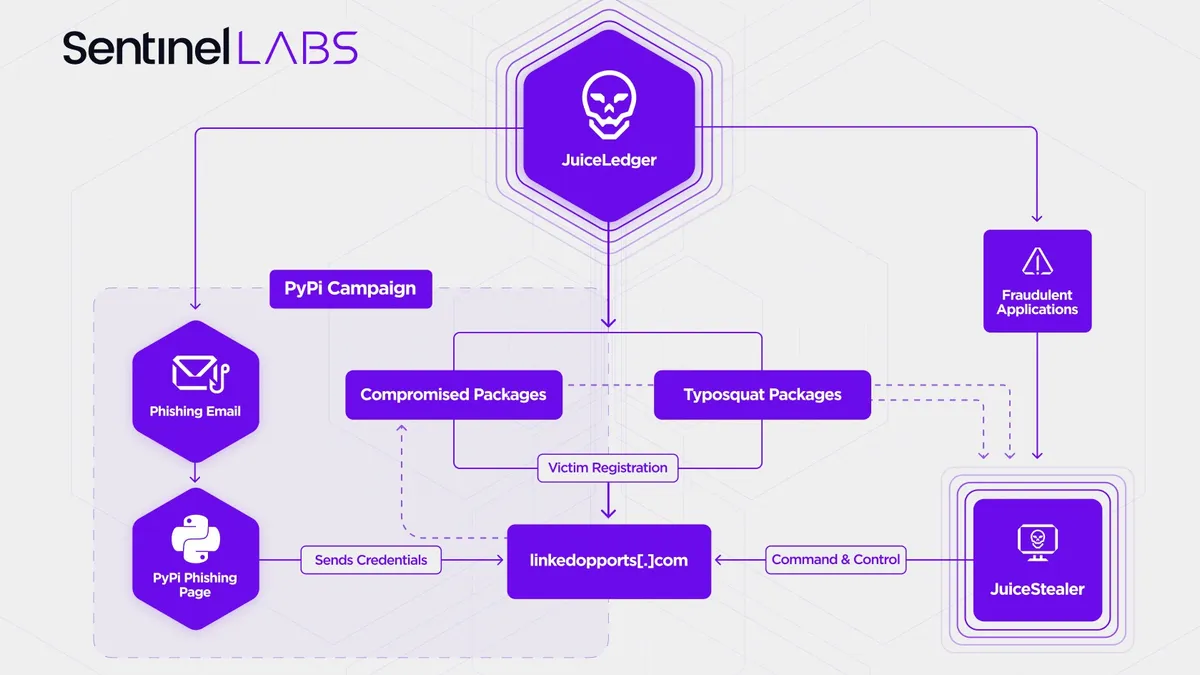
PyPI contributors targeted by JuiceLedger in latest attack against open source
The supply chain attack represents a potential risk to organizations using open source, researchers from SentinelOne and Checkmarx say.
By David Jones • Sept. 6, 2022 -
Okta CEO pushes for passwordless future in wake of phishing attacks
Customers that rely on passwords and log-in pages are putting their organizations at greater risk of attack, Todd McKinnon told analysts.
By Matt Kapko • Sept. 2, 2022 -
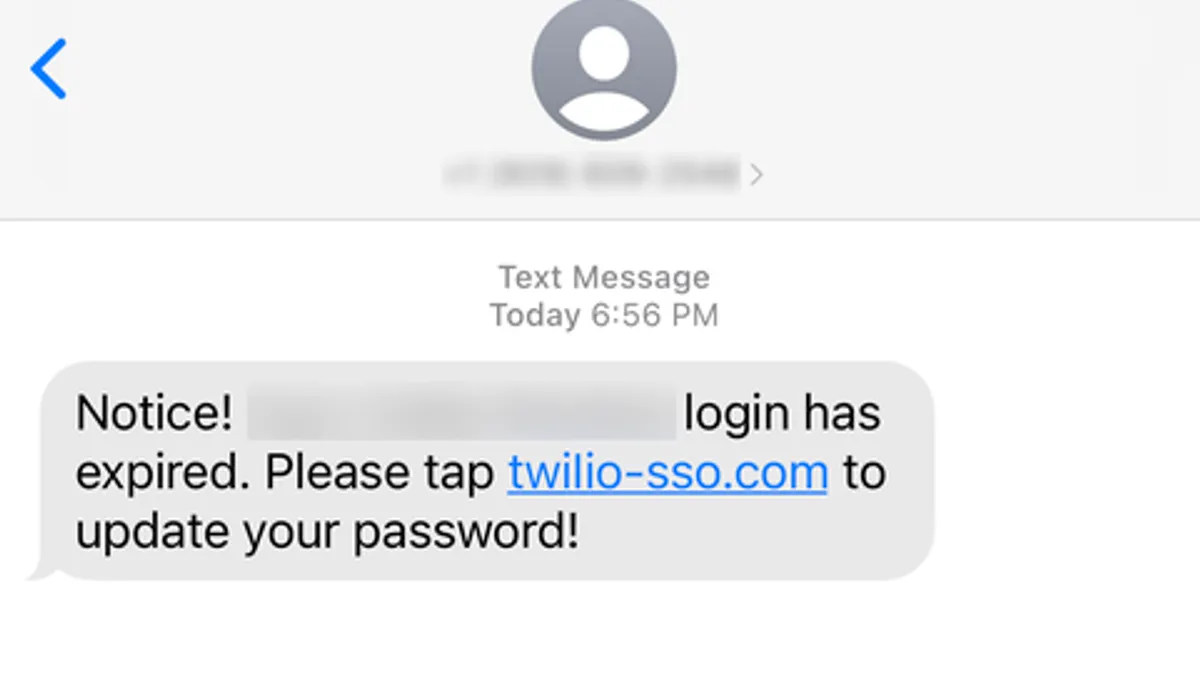
Okta entangled by Twilio phishing attack
The threat actor initiated one-time password requests as they searched dozens of phone numbers linked to a single targeted organization.
By Matt Kapko • Aug. 30, 2022 -
Twilio discloses more victims as phishing attack effects cascade
The communications and identity authentication provider said it has discovered 163 victims thus far.
By Matt Kapko • Aug. 29, 2022 -
Sponsored by Delinea
How does Privileged Access Management work?
The model is a framework to help you set the right PAM foundation and get your organization on the PAM journey, now and in the future.
Aug. 29, 2022 -
Tips for how to safeguard against third-party attacks
Organizations need to demand and ensure all vendors implement rigorous security measures. Sometimes the least likely tools pose the most risk.
By Matt Kapko • Aug. 25, 2022 -
Ransomware attack surges tied to crypto spikes
Not every ransomware attempt leads to a successful attack. But with more attempts comes more potential damage.
By Matt Kapko • Aug. 24, 2022 -
Credential stuffing hammers US businesses as account data for sale in bulk
Media companies, retailers, restaurant groups and food delivery services are at heightened risk, the FBI said.
By Matt Kapko • Aug. 23, 2022 -
Third-party attacks spike as attackers target software connections
Every third-party tool and partnership is a potential path for attack and an opportunity to exploit human behavior. The risks spread far and wide.
By Matt Kapko • Aug. 22, 2022 -
LockBit ransomware group claims responsibility for Entrust attack
The prolific ransomware gang threatened to publish data stolen during the attack.
By Matt Kapko • Aug. 19, 2022 -
Mailchimp breach shines new light on digital identity, supply chain risk
Sophisticated threat actors are targeting weak links in the email marketing space to go after vulnerable financial targets.
By David Jones • Aug. 18, 2022 -
DigitalOcean, caught in Mailchimp security incident, drops email vendor
An attack on the email marketing firm raises questions about the continued risk of a supply chain compromise.
By David Jones • Aug. 17, 2022 -
Twilio phishing attack fallout spreads to Signal
The vendor’s widely used two-factor authentication service became a point of potential compromise for 1,900 Signal users. One user suffered a direct hit.
By Matt Kapko • Aug. 15, 2022 -
How attackers are breaking into organizations
Threat actors lean heavily on phishing attacks, vulnerabilities in software and containers, and stolen credentials, according to top cyber vendor research.
By Matt Kapko • Aug. 15, 2022 -
Internal Cisco data stolen after employee hit by voice phishing attack
Cisco identified the attacker as an initial access broker with ties to multiple cybercrime and ransomware groups.
By Matt Kapko • Aug. 11, 2022 -
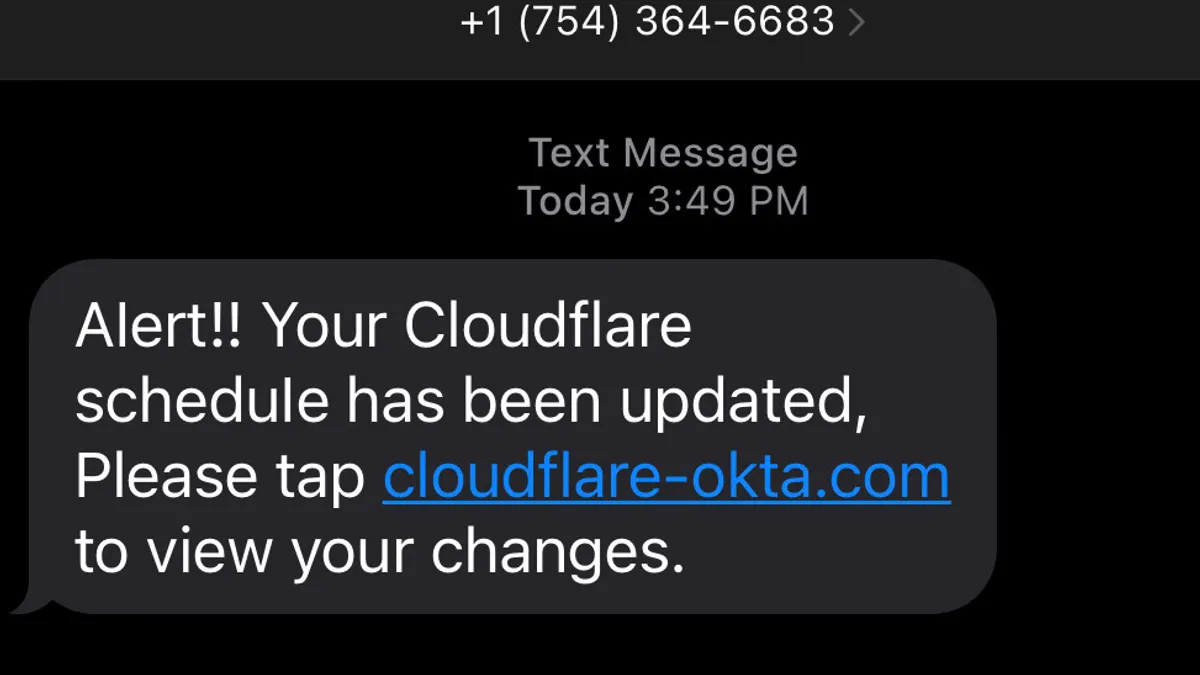
Cloudflare thwarts ‘sophisticated’ phishing attack strategy that bruised Twilio
Dissimilar responses from Cloudflare and Twilio bear important lessons in transparency, resiliency and access.
By Matt Kapko • Aug. 9, 2022 -
Twilio employees duped by text message phishing attack
The communications provider declined to say how many employees were duped and the amount of customers compromised.
By Matt Kapko • Aug. 8, 2022 -
Encevo stays resilient post-attack, but it’s still assessing the data damage
The Luxembourg energy supplier’s ability to thwart a shutdown likely empowered its refusal to pay a ransom.
By Matt Kapko • Aug. 8, 2022