Cyberattacks: Page 27
-
Sinclair Broadcast still assessing financial impact of ransomware attack
While the news provider maintains cyber insurance to cover losses related to security risk and business interruption, such policies may not be enough to cover the losses, President and CEO Chris Ripley said.
By David Jones • Nov. 4, 2021 -
SolarWinds threat actor targets cloud services, Microsoft 365 mailboxes
The threat actor is using a tactic called EWS impersonation to target mailboxes in Microsoft 365 and is also using cloud service providers to target end users, Mandiant researchers said.
By David Jones • Nov. 1, 2021 -
 Explore the Trendline➔
Explore the Trendline➔
 BNMK0819 via Getty Images
BNMK0819 via Getty Images Trendline
TrendlineTop 5 stories from Cybersecurity Dive
A wave of rules, regulations and federal action is putting pressure on businesses to shore up security amid a backdrop of emboldened threat actors has a nice ring to it.
By Cybersecurity Dive staff -
The most 'anxiety-inducing' cyberattacks of 2021 for IT and security
"PrintNightmare is just like the flipping gift that keeps on giving," Jason Slagle of CNWR IT Consultants said. "You can get popped by it, and then literally every week there's some sort of update."
By Samantha Schwartz • Oct. 29, 2021 -
Identity crisis: Why ransomware groups rebrand — and disappear
Criminals are not known for telling the truth, but what they say is usually the only explanation for a disappearance. Even if it is a lie.
By Samantha Schwartz • Oct. 28, 2021 -
SolarWinds threat actor targeted IT service providers in thousands of attacks, Microsoft says
The campaign from the Russian nation-state threat actor Nobelium was caught early, but there were at least 14 compromises involving password spraying and phishing to gain access.
By Samantha Schwartz • Oct. 25, 2021 -
Sponsored by Cybersource
How businesses are tackling fraud in a digital-first reality
With digital transactions and eCommerce continuing to grow in volume, successfully taking on fraud will require businesses to explore and rely on new tools and technologies.
Oct. 25, 2021 -
Sinclair Broadcast becomes latest media group to face ransomware attack
Researchers linked the incident that disrupted weekend broadcasts to Evil Corp., which used a ransomware strain associated with WastedLocker.
By David Jones • Updated Oct. 21, 2021 -
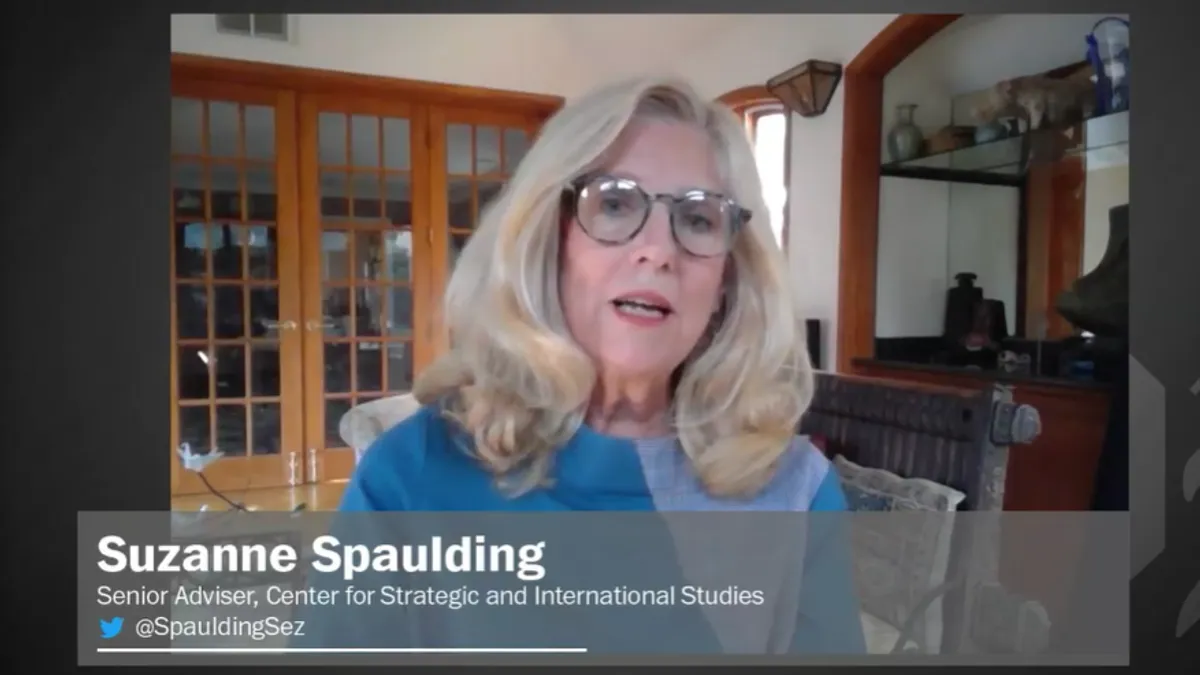
The public needs to understand what's at stake with cyberattacks, DHS adviser says
The Colonial Pipeline cyberattack was a "crisis of communication" between the company and consumers, Homeland Security Adviser Suzanne Spaulding said.
By Samantha Schwartz • Oct. 15, 2021 -
Users have bad security habits. What can businesses do?
"As strange as it sounds, in the case of a security incident in the enterprise, you can't blame the user," Bitdefender's Alex "Jay" Balan said.
By Samantha Schwartz • Oct. 14, 2021 -
Opinion
How to secure the enterprise against REvil-style attacks
There is no way to fully protect against advanced attacks such as zero-day vulnerabilities or nation-state threats — responding quickly is critical to minimizing damage.
By Chris Silva • Oct. 12, 2021 -
War room preparation key to ransomware response, experts say
Companies need to assemble stakeholders ahead of an attack and be ready for potential fallout from litigation, reputational risk and operations disruption.
By David Jones • Oct. 11, 2021 -
Why CEOs become communication chiefs after a cyberattack
When ransomware hit, the CEOs of Colonial Pipeline and Accellion paused their day-to-day duties. Their immediate new roles? Communication.
By Samantha Schwartz • Oct. 7, 2021 -
REvil, DarkSide highlight surge in Q2 ransomware attacks: report
The government sector saw more ransomware attacks, while financial services companies faced increased threats in the cloud, according to McAfee Enterprise research.
By David Jones • Oct. 4, 2021 -
Ransomware attacks put availability of medical devices at risk: FDA cyber chief
Industry reached a "watershed moment" earlier this year when a device outage caused by malware endangered patient lives, said the acting director of cybersecurity at CDRH.
By Greg Slabodkin • Oct. 4, 2021 -
Microsoft warns of new credential-stealing backdoor from SolarWinds threat actor
The newly identified malware, called FoggyWeb, has been observed since April and is used to steal from compromised AD FS servers.
By David Jones • Sept. 28, 2021 -
25% of providers saw mortality rates rise after ransomware attacks, survey finds
This study of health delivery organizations is one of the first finding a direct impact on patient care. It comes roughly a year after a patient in Germany died as a result of delayed care following a ransomware attack.
By Rebecca Pifer • Sept. 27, 2021 -
Ripple effects from a cyber incident take a year to develop: report
Organizations are likely to both generate and suffer the downstream consequences of cyber incidents because of the technological reliance companies have on one another.
By Samantha Schwartz • Sept. 27, 2021 -
Ransomware compromises customer data in farm co-op attack
A Minnesota-based co-op became the second agricultural firm in recent days to be the target of ransomware, just weeks after the FBI and CISA warned of a wider threat to the industry.
By David Jones • Updated Sept. 24, 2021 -
BlackMatter gang targets Iowa agriculture cooperative in a test of critical infrastructure
Iowa-based New Cooperative, one of the largest grain suppliers in the state, is facing a demand to pay $5.9 million in ransom.
By David Jones • Sept. 21, 2021 -
What to know about software bill of materials
The Biden administration wants more transparency in the software supply chain. Will private industry join in?
By Samantha Schwartz • Sept. 20, 2021 -
Companies must develop operational plan for ransomware recovery
In the face of more frequent and sophisticated attacks, companies need to identify their most critical assets and work to limit cyberattack fallout.
By David Jones • Sept. 17, 2021 -
'Big game hunters': Ransomware groups target their perfect victim
Research from KELA found U.S. companies with upwards of $100 million in revenue are favored targets.
By Samantha Schwartz • Sept. 13, 2021 -
What ransomware negotiations look like
Fear can overwhelm the decision of whether to pay a ransom. But in negotiations, companies have to take a backseat.
By Samantha Schwartz • Sept. 9, 2021 -
What's at stake in a credential stuffing attack
Attackers gain a network foothold by using stolen credentials under the guise of an authenticated trusted employee or third party.
By Sue Poremba • Sept. 1, 2021 -
Why a ban on ransom payments will not work
Those most impacted by an attack are motivated to pay. In some cases, it's not the victim company but its customers who want service restored.
By Samantha Schwartz • Aug. 27, 2021