Vulnerability: Page 2
-
Top US senator calls out supply-chain risk with DoD contractors
The Senate Intelligence Committee chairman questioned the security of Microsoft’s “digital escort” arrangement with its Chinese employees.
By Eric Geller • Updated July 18, 2025 -
Researchers warn of cyberattacks targeting key Fortinet software
Experts urged Fortinet customers to immediately apply patches or disable the affected administrative interface.
By David Jones • Updated July 18, 2025 -
Threat actor targets end-of-life SonicWall SMA 100 appliances in ongoing campaign
The hacker has deployed a backdoor to modify the boot process and has exploited several different vulnerabilities during the attack spree.
By David Jones • July 16, 2025 -
Risk management, legacy tech pose major threats to healthcare firms, report finds
Companies have improved their recovery processes and user controls but still lag in risk preparedness, according to the report.
By Eric Geller • July 15, 2025 -
Hackers exploiting flaw in widely used Wing FTP Server
Researchers warn that a vulnerability in the file-transfer service could enable remote code execution.
By David Jones • Updated July 14, 2025 -


Retrieved from Norfolk Southern

Major railroad-signaling vulnerability could lead to train disruptions
The high-severity flaw could let a hacker abruptly halt — and potentially derail — a train.
By Eric Geller • Updated July 14, 2025 -
Businesses are overconfident as mobile phishing scams surge
Nearly six in 10 companies experienced incidents because of voice or text phishing attacks that led to executive impersonation, according to a new report from Lookout.
By Eric Geller • July 11, 2025 -


Citrix via Flickr

Researchers, CISA confirm active exploitation of critical Citrix Netscaler flaw
Critics have faulted Citrix for not updating its guidance in recent days, even as concerns grow about a resumption of the 2023 CitrixBleed crisis.
By David Jones • Updated July 11, 2025 -
Sponsored by Tines
Beyond the hype: How security leaders can build AI agents that matter
AI agents can reclaim hours of lost analyst time if deployed with purpose, strategy and secure design.
By Eoin Hinchy, CEO & Co-Founder, Tines • June 30, 2025 -


stock.adobe.com/Malambo C/peopleimages.com
 Sponsored by Imprivata
Sponsored by ImprivataWhy IT teams under pressure are looking to access logs for answers
Under pressure, IT teams are tapping access logs for real-time insight—not just compliance.
By Joel Burleson-Davis, Chief Technology Officer, Imprivata • June 30, 2025 -
Most building management systems exposed to cyber vulnerabilities, experts warn
A study of over 467,000 building management systems across 500 organizations found that 2% of all devices essential to business operations had the highest level of risk exposure.
By Joe Burns • June 27, 2025 -


Citrix via Flickr

Hackers exploiting critical Citrix Netscaler flaw, researchers say
After confirming exploitation of a separate zero-day flaw, Cloud Software Group promises to be transparent.
By David Jones • June 27, 2025 -
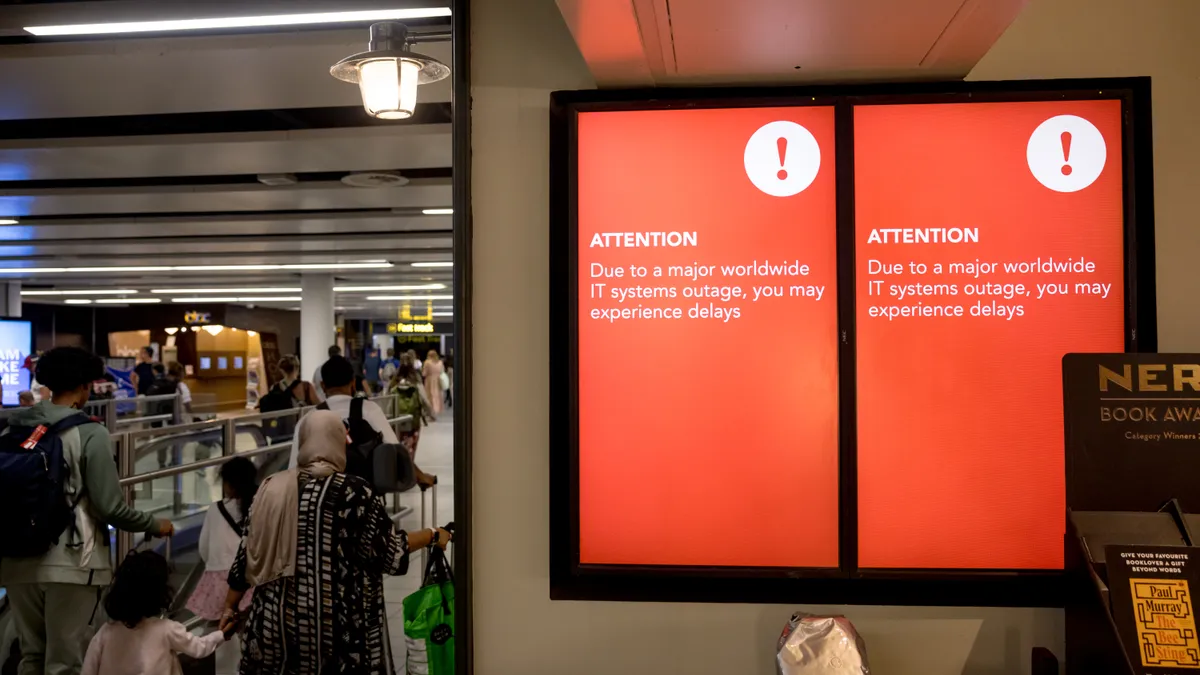
Microsoft to make Windows more resilient following 2024 IT outage
The company has been working with security partners to make sure future software updates don’t lead to operational disruptions for customers.
By David Jones • Updated June 26, 2025 -
Critical vulnerability in Citrix Netscaler raises specter of exploitation wave
Threat researchers warn the flaw could open up a flood of attacks that rival the 2023 CitrixBleed crisis.
By David Jones • Updated June 25, 2025 -
Researchers urge vigilance as Veeam releases patch to address critical flaw
The patch for a previously disclosed vulnerability in the company’s backup software did not offer adequate protection, according to researchers.
By David Jones • June 18, 2025 -
Cloud storage buckets leaking secret data despite security improvements
New data from Tenable highlighted significant improvements in the number of businesses with publicly exposed and critically vulnerable buckets storing sensitive data.
By Eric Geller • June 18, 2025 -
Critical Zyxel vulnerability under active exploitation after long period of quiet
Researchers say a sudden burst of activity could be linked to a Mirai botnet variant.
By David Jones • June 17, 2025 -
CISA warns of supply chain risks as ransomware attacks exploit SimpleHelp flaws
The latest confirmed cyber intrusion hit a utility billing software provider and its customers.
By Eric Geller • June 13, 2025 -
Software vulnerabilities pile up at government agencies, research finds
A Veracode report reveals that government networks have accumulated years of unresolved security flaws, putting them at serious risk of exploitation.
By David Jones • June 12, 2025 -
Critical flaw in Microsoft Copilot could have allowed zero-click attack
Researchers said the vulnerability, dubbed “EchoLeak,” could allow a hacker to access data without any specific user interaction.
By David Jones • Updated June 11, 2025 -
From malware to deepfakes, generative AI is transforming attacks
Generative AI is even helping hackers trick open-source developers into using malicious code, according to Gartner.
By Eric Geller • June 10, 2025 -
SentinelOne rebuffs China-linked attack — and discovers global intrusions
The security firm said the operatives who tried to breach it turned out to be responsible for cyberattacks on dozens of critical infrastructure organizations worldwide.
By Eric Geller • Updated June 9, 2025 -
Sponsored by ThreatLocker
Understanding the evolving malware and ransomware threat landscape
Cyber threats like ransomware and malware are rising fast, hitting firms like Frederick Health and Marks & Spencer. Defense needs layers, adaptability and vigilance.
By Farid Mustafayev, Senior Software Engineer, ThreatLocker • June 9, 2025 -

 (2025). "EPA Administrator Lee Zeldin Launches the Greatest Day of Deregulation in American History" [Video]. Retrieved from U.S. Environmental Protection Agency.
(2025). "EPA Administrator Lee Zeldin Launches the Greatest Day of Deregulation in American History" [Video]. Retrieved from U.S. Environmental Protection Agency.
Water utilities mitigate equipment flaws after researchers find widespread exposures
Censys researchers said hundreds of water treatment facilities have taken steps to protect against malicious cyber intrusions.
By David Jones • June 5, 2025 -
Vast array of solar power equipment left exposed online
The most commonly exposed device has been discontinued and vulnerable for a decade, new research found.
By Eric Geller • June 4, 2025